Nexus S (I902x) bootloader¶
- Table of contents
- Nexus S (I902x) bootloader
The Nexus S (I902x) comes with a bootrom and a set of two proprietary bootloaders. The bootrom: internal ROM (iROM) is stored read-only on the S5PC110 SoC chip. It loads the first bootloader: Samsung Primitive Bootloader (PBL), which loads the second bootloader: Samsung Secondary Bootloader (SBL). These bootloaders are proprietary software.
More information on the booting sequence is available on the S5PC110 User Manual, section 2 (System), part 6 (Booting sequence).
Boot device priority¶
The S5PC110 bootrom (iROM) allows booting from various devices such as NAND, MMC, eMMC, UART and USB. The boot device priority is selected using the Operating Mode (OM) pins. Boolean values for each pin depend on the voltage applied to the pin: a positive voltage represents a logical 1 while ground represents a logical 0.
OM_STAT register¶
The OM_STAT register holds the value of the OM pins. It is available at address: 0xe010e100.
The register value can be read using:
# devmem 0xe010e100 8 0x09
OM resistors¶
OM pins are set to boolean values using pull-up (logical 1) and pull-down (logical 0) resistors. The Nexus S (I902x) schematics show all the possible resistors connected to the pins.
According to the Nexus S (I902x) Schematics:
Only a few are actually populated on the board:
According to the Nexus S (I902x) Service Manual: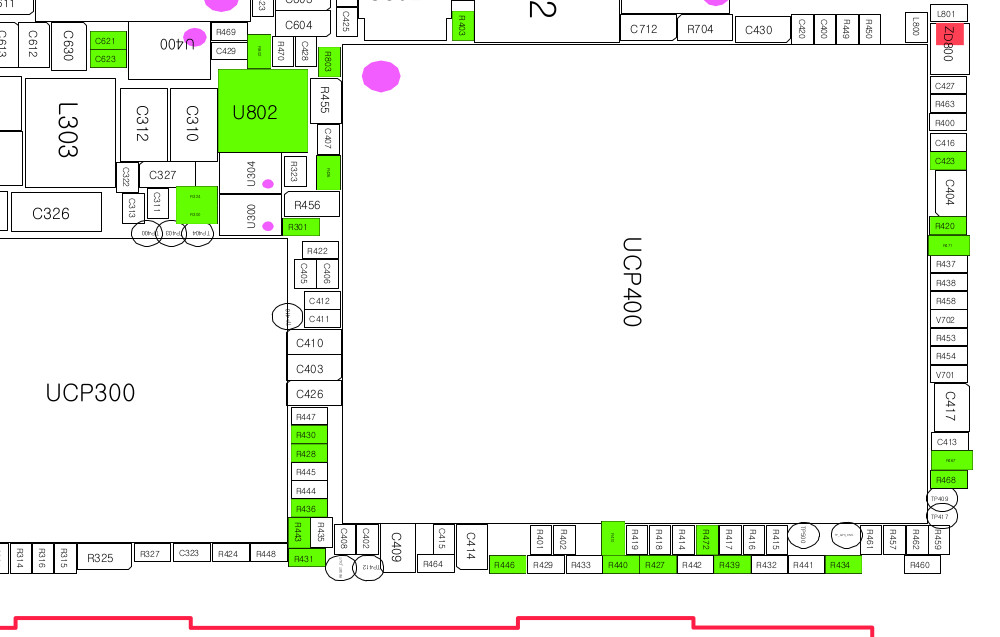
Resistors highlighted in green are not populated on the board. Hence, the actual layout is the following:
| XOM5 | XOM4 | XOM3 | XOM2 | XOM1 | XOM0 | |
|---|---|---|---|---|---|---|
| Pull-up resistor | N/A | N/A | R429 | N/A | N/A | R435 |
| Pull-down resistor | R448 | R447 | N/A | R445 | R444 | N/A |
| Boolean value | 0 | 0 | 1 | 0 | 0 | 1 |
First boot device¶
According to the S5PC110 User Manual, section 2 (System), part 6.2.4 (OM pin configuration), table 6-3, such a value (0x04) indicates OnenandMux as first boot device.
Secure boot¶
According to the S5PC110 User Manual, section 2 (System), part 6 (Booting sequence), the bootrom (iROM) found on the S5PC110 SoC implements secure boot, which is enabled depending on the value of an e-fuse:
If you select secure booting, iROM code and first boot loader provide integrity checking function (that is it uses public key algorithm) to verify loaded image. There are 160 e-fuse bits of secure boot key, and they are used to authenticate loaded public key before the iROM’s integrity check.
This implies that in secure boot mode, the bootrom (iROM) will check the signature of the first bootloader and refuse to boot if the signature doesn't match the secure boot key. More information on this topic is available on the S5PC110 User Manual, section 2 (System), part 6.2.2 (Booting sequence example), figure 6-2.
On the Nexus S (I902x), secure boot mode appears to be enabled: changing a single byte on the first bootloader ended up in the system refusing to boot. In addition, a few messages from the bootloaders output suggest that such signature checks are enforced: IROM e-fused - Secure Boot Version.
SECKEY register¶
The SECKEY register holds the public key that is used to check the bootloaders signatures. It is available at address 0xe0e00000, as mentioned on the S5PC110 User Manual, section 1 (Overview), part 2.1.2 (Special function register map). The register is e-fused and cannot be overwritten on the Nexus S (I902x).
Access to the register requires the CLK_SECKEY clock to be enabled, as mentioned on the S5PC110 User Manual, section 2 (System), part 3.7.5.6 (Clock gating control register).
The seckey clock can be enabled at boot-time using the following kernel patch:
diff --git a/arch/arm/mach-s5pv210/clock.c b/arch/arm/mach-s5pv210/clock.c
index 6d3e609..38ebb76 100644
--- a/arch/arm/mach-s5pv210/clock.c
+++ b/arch/arm/mach-s5pv210/clock.c
@@ -1479,6 +1479,7 @@ void __init_or_cpufreq s5pv210_setup_clocks(void)
unsigned int ptr;
u32 clkdiv0, clkdiv1;
struct clksrc_clk *pclkSrc;
+ int i;
/* Set functions for clk_fout_epll */
clk_fout_epll.enable = s5p_epll_enable;
@@ -1564,6 +1565,16 @@ void __init_or_cpufreq s5pv210_setup_clocks(void)
/* Display the clock source */
s3c_set_clksrc(pclkSrc, true);
}
+
+ for (i = 0; i < ARRAY_SIZE(init_clocks_off); i++) {
+ if (init_clocks_off[i].name == NULL)
+ break;
+
+ if (strcmp("seckey", init_clocks_off[i].name) == 0) {
+ printk(KERN_INFO "%s: Enabling seckey clock\n", __func__);
+ clk_enable(&init_clocks_off[i]);
+ }
+ }
}
static struct clk *clks[] __initdata = {
The register value can then be read using:
# devmem 0xE0E00018 32 0x07F0600F
A non-zero value on the register indicates that secure boot is enabled, while a zero value indicates that secure boot is disabled. Hence, secure boot is enabled on the Nexus S (I902x).
Bootloaders secure boot¶
The first bootloader (PBL) appears to be implementing and enforcing a similar secure boot mechanism. However, there is no signature check enforced regarding the Linux kernel.
Since signature checks are enforced by the bootrom and provided that there is apparently no easy way of replacing the public key the signatures are checked against, running free software bootloaders on the Nexus S (I902x) seems impossible.
It is however possible to run a free software bootloader (U-Boot) as second bootloader using a version of the first bootloader (PBL) that does not enforce the signature check.
Bootloaders output¶
----------------------------------------------------------- Samsung Primitive Bootloader (PBL) v3.0 Copyright (C) Samsung Electronics Co., Ltd. 2006-2010 ----------------------------------------------------------- Muxed [[OneNAND]] 512MB (0x50) Sync Scanning Bad Block ....... Bad Block 77 (5) Bad Block 295 (5) Bad Block 1232 (5) Bad Block 1646 (5) Bad Block 1831 (5) Bad Block 2047 (0) SBL loadding success Set cpu clk. from 400MHz to 800MHz. OM=0x9, device=OnenandMux(Audi) IROM e-fused - Secure Boot Version. ----------------------------------------------------------- Samsung Secondary Bootloader (SBL) v3.0 Copyright (C) Samsung Electronics Co., Ltd. 2006-2010 Board Name: HERRING REV 52 Build On: Jan 20 2011 17:19:41 ----------------------------------------------------------- MMC SEM16G 15188 MB Re_partition: magic code(0x0) Muxed [[OneNAND]] 512MB (0x50) Sync Scanning Bad Block ....... Bad Block 77 (5) Bad Block 295 (5) Bad Block 1232 (5) Bad Block 1646 (5) Bad Block 1831 (5) Bad Block 2047 (0) Partitions loading success Read image(PARAM) from flash ....... Done init_fuel_gauge: vcell = 4083mV, soc = 94 PMIC_IRQ1 = 0xc0 PMIC_IRQ2 = 0x0 PMIC_IRQ3 = 0x0 PMIC_IRQ4 = 0x0 PMIC_STATUS1 = 0x0 PMIC_STATUS2 = 0x0 PMIC_STATUS3 = 0x0 PMIC_STATUS4 = 0x0 PMIC_STATUS5 = 0x0 PMIC_SMPL = 0x0 Key scan = 0x0 message.command = message.status = message.recovery = BOOT_MODE_NORMAL (SW_RST(0x00000004), INFORM(0x000000ee)) LCD ID = 0x0060a953 Done Kernel(boot.img) read success from partition no.5 Setting param.serialnr = 0x3733bab6 0x6de200ec Setting param.board_rev = 0x34 Setting param.cmdline = console=ttyFIQ0 no_console_suspend androidboot.serialno=3733BAB66DE200EC androidboot.bootloader=I9020XXKA3 androidboot.baseband=I9020XXKB3 androidboot.info=0x4,0xee,1 androidboot.carrier=EUR gain_code=3 s3cfb.bootloaderfb=0x34a00000 mach-herring.lcd_type=0x00000000 oem_state=unlocked Setting param.initrd_start = 0x31000000, param.initrd_size = 0x23265 Starting kernel at 0x30008000... Uncompressing Linux... done, booting the kernel.
References¶
- S5PC110 User Manual: http://dl.project-voodoo.org/archives/documentation/S5PC110_EVT1_UM10.pdf
- Nexus S (I902x) Service Manual and Schematics: http://mobilcoms.ru/load/1-1-0-4499
These documents are the propriety of Samsung Electronics and are not hosted by the Replicant project.
However, some excerpts from these documents are provided, for the purpose of providing technical evidence of the facts that are mentioned in this page. We believe that this particular use of the copyrighted work is fair use.
- Create your own I9000/S8500 (& all S5PC110 based devices) bootloader&ultimate unbrick (XDA): http://forum.xda-developers.com/showthread.php?t=1233273
- Hummingbird Interceptor BootLoader: https://code.google.com/p/hummingbird-hibl/
- U-Boot second bootloader port: https://github.com/hackqiang/crespo-bootloader
- Bootrom (iROM) dump and disassembly: https://github.com/OSLL/boots/tree/master/S5PC110
Updated by Denis 'GNUtoo' Carikli about 4 years ago · 19 revisions